SECURITY
Glider's Guide to PCI Compliance
The need for organisations to be PCI compliant is greater than ever. Read on for tips and guidance on how to do this.
What is PCI DSS?
PCI DSS stands for Payment Card Industry Data Security Standard. The security standard was started in 2004 by Visa, Mastercard, American Express, Discover and JCB.
To help with managing compliance standards, the payment brands also established the PCI Security Standards Council (PCI SSC) in 2006 as an independent body, in order to “monitor threats and improve the industry’s means of dealing with them, through enhancements to PCI Security Standards and by the training of security professionals”.
Does PCI DSS affect my organisation?
If you accept, process, store or transmit card data then PCI DSS affects your organisation. Cardholder data is continuously at risk of theft from hackers that are on the lookout for a way to exploit potential weaknesses in your organisation. So, no matter the size of your business, PCI DSS is there to protect your customers and their data, assisting in the prevention of a data breach which could have a huge impact.
What does PCI compliance mean?
The PCI DSS refers to payment security standards that ensure all organisations (involved in payment card processing) safely and securely accept, store, process, and transmit cardholder data (also known as your customers’ credit card information) during a credit card transaction.
Any merchant with a merchant ID that accepts payment cards must follow these PCI-compliance regulations to protect against data breaches. The requirements range from establishing data security policies for your business and employees to removing card data from your processing systems and payment terminals.
Who enforces PCI compliance?
The Payment Card Industry Security Council (PCI SSC) was formed in 2006 to manage the ongoing evolution of the payment card industry. The PCI SCC continues to administer the guidelines with a focus on improving payment account security throughout the transaction process.
However, it is the payment brands (Visa, Mastercard, American Express, Discover and JCB) and acquirers (banks), not the PCI council, that are responsible for enforcing compliance and are able to issue fines and restrictions on your ability to accept card payments.
Who needs PCI DSS compliance certification?
Although there is technically no such thing as “PCI certification,” entities of all sizes, service providers, banks, and any other organisation that process credit and debit card payments need to prove they are PCI compliant.
Are debit card transactions in scope?
In-scope cards include any debit, credit, and pre-paid cards branded with one of the five card association/brand logos that participate in the PCI SSC – American Express, Discover, JCB, MasterCard, and Visa.
How often is the PCI Data Security Standard updated?
There is no hard and fast rule for how often the standard is updated, but on average it has been updated once every two years.
What is cardholder data?
The PCI SSC defines cardholder data’ in their Glossary as follows:
PAN Acronym for “Primary Account Number” and also referred to as “account number.” Unique payment card number (typically for credit or debit cards) that identifies the issuer and the particular cardholder account.
Service Code Three-digit or four-digit value in the magnetic-stripe that follows the expiration date of the payment card on the track data. It is used for various things such as defining service attributes, differentiating between international and national interchange, or identifying usage restrictions.
Magnetic Stripe Data Also referred to as “full track data” or “track data.” Data encoded in the magnetic stripe or chip used for authentication and/or authorization during payment transactions. This can be the magnetic-stripe image on a chip or the data on the track 1 and/or track 2 portion of the magnetic stripe.
Sensitive Authentication Data Security-related information (including but not limited to card validation codes/values, full track data (from the magnetic stripe or equivalent on a chip), PINs, and PIN blocks) used to authenticate cardholders and/or authorize payment card transactions.
Card Verification Code Also known as Card Validation Code (CVC) or Value (CVV), or Card Security Code (CSC), or Card Identification Number (CID), or Card Verification Data (CVD). This refers to either: (1) magnetic-stripe data, or (2) printed security features.
PIN Acronym for “Personal Identification Number.” Secret numeric password known only to the user and a system to authenticate the user to the system. The user is only granted access if the PIN they provide matches the PIN in the system. Typical PINs are used for automated teller machines (ATMs) for cash advance transactions. Another type of PIN is one used in EMV chip cards where the PIN replaces the cardholder’s signature.
All these elements constitute cardholder data, and therefore fall under the jurisdiction of the PCI DSS.
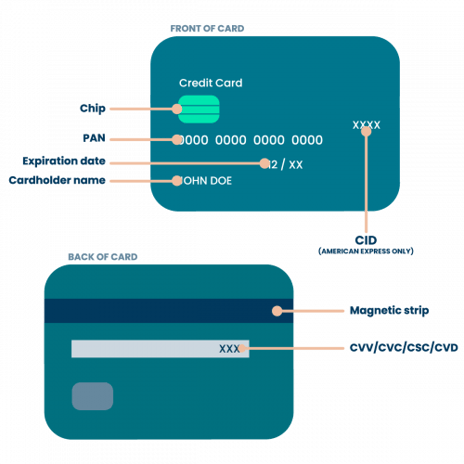
The credit card diagram above displays where unique and sensitive cardholder data is contained in a credit or debit card. Your organisation should avoid storing any of the data in this diagram; if you do, then you’ll likely be required to present a good business reason for storage and demonstrate that you have the proper mechanisms in place to protect it. If the cardholder name, expiration date and/or service code (CVV/CVC/CSC/CVD) are stored, processed or transmitted with the PAN, they must be protected in accordance with PCI DSS requirements.
Where might cardholder data be stolen from?
To identify where your organisation might be vulnerable to an attack, it’s important to be aware of the places where cardholder data can be stolen from. For example, data can be stolen from:
- Compromised card readers
- Insecure payment system databases
- Hidden cameras recording entry of authentication data
- A secret tap into your wireless or wired network
- Paper stored in a filing cabinet or written note
Therefore, it’s important to secure the entire payment life cycle, from credit card acceptance to payment processing, by protecting cardholder data where it is captured and as it flows into the payment system to your merchant account.
What needs to be secure?
It is essential to not store any cardholder data in the below list of systems, card reading terminals and filing systems:
- Card readers
- Point of sale systems
- Networks and wireless access routers
- Payment card data storage and transmission
- Payment card data stored in paper-based records
- Online payment applications and shopping carts
What does it cost to be PCI DSS compliant?
The fees to become PCI compliant, and maintain that standing annually, can range from approximately $1,000 annually to over $50,000 annually, depending on the size of your business.
What are the consequences of non-compliance?
While PCI compliance is not a law, compliance is still a big deal. It’s your responsibility to ensure that your customers’ cardholder data is safeguarded, free from exposure from customer service representatives, fraudulent attacks (internal and external) and other security breaches. By achieving PCI compliance and adhering to the comprehensive requirements of PCI DSS, your organisation can be confident that you are improving the safety of your customer’s data and the way payments are processed.
If your business does not comply with the PCI standards, you could be at risk for data breaches, fines, card replacement costs, costly forensic audits and investigations into your business, brand damage, and more if a breach occurs.
The payment brands may, at their discretion, fine an acquiring bank $5,000 to $100,000 per month for PCI compliance violations. The banks will most likely pass this fine along until it eventually hits the merchant. Furthermore, the bank will also most likely either terminate your relationship or increase transaction fees. Penalties are not openly discussed nor widely publicised, but they can be catastrophic to a small business. It is important to be familiar with your merchant account agreement, which should outline your exposure.
Aside from the financial cost, there are also other potential liabilities that could affect your business. According to PCI Security Standards, failing to comply with the PCI standards and resulting data breaches could result in:
- Lost confidence, so customers go to other merchants
- Diminished sales
- Cost of reissuing new payment cards
- Fraud losses
- Higher subsequent costs of compliance
- Legal costs, settlements, and judgments
- Fines and penalties
- Termination of ability to accept payment cards
- Lost jobs (CISO, CIO, CEO, and dependent professional positions)
PCI DSS and Call Recording
It is common practice nowadays for organisations to record telephone calls between staff and customers. This might be for quality control, for staff monitoring and training, or as part of customer service and complaints review. In many industries (particularly financial services) the recording of calls is a regulatory requirement.
The PCI DSS on the other hand, outlines that in order to be compliant no card sensitive data can be recorded or stored by the organisation. This presents a challenge for any organisation who wants to accept card payments over the phone but is also required to make and store recordings of every conversation.
Call recording platforms have introduced a number of different ways of excluding numbers from recordings:
- Pause and resume – manually or automatically pausing and unpausing call recorders when card details are provided.
- Mute or mask – apply a filter which mutes or masks the audio when the card details are read out.
- Keypad payment – card details are keyed in on a telephone keypad during the call.
None of these approaches are 100% foolproof, and certainly with manual techniques, there is always the risk of human error leaving you exposed to a breach.
Fortunately there’s a new way to take card payments over the phone that enables you to record the whole of the call whilst remaining fully PCI DSS compliant. Using Glider Agent Assisted Payments, customers are presented with a way to pay directly from their mobile phone. Agents cannot hear or see the sensitive card information, nor can the card details be picked up in call recordings so there’s no way that the caller’s card details can be identified – even if someone was able to access to your organisation’s call recordings.
What does de-scoping mean?
PCI DSS considers any person, system, or piece of technology that touches payment information as “in-scope”.
For example, customer service agents, telephony systems and the IT network and databases used to take payments are all in scope for compliance and should be reviewed as part of the 12 PCI-DSS requirements.
To reduce the scope of compliance for your organisation and the number of PCI controls you need to implement, you can decrease the number of staff and systems that are involved in card payment processing by “de-scoping” them. Glider’s Agent Assisted Payments solution is able to assist you in de-scoping Agents, telephony systems and the technology required to record phone calls – meaning a quicker and less expensive journey to PCI compliance.
What are the 12 PCI DSS requirements?
- Install and maintain a firewall configuration to protect cardholder data
- Do not use vendor-supplied defaults for system passwords and other security
parameters - Protect stored cardholder data
- Encrypt transmission of cardholder data across open, public networks
- Protect all systems against malware and regularly update antivirus software or
programs - Develop and maintain secure systems and applications
- Restrict access to cardholder data by business need to know
- Identify and authenticate access to system components
- Restrict physical access to cardholder data
- Track and monitor all access to network resources and cardholder data
- Regularly test security systems and processes
- Maintain a Security Policy that addresses information security for all personnel
What are the PCI DSS compliance levels?
There are four levels of PCI compliance; each level has unique requirements for a business to validate its compliance. The level under which your business falls is based on your total transaction volume, annually.
Level 1: A merchant processing over 6m VISA and MasterCard transactions p/a
Level 2: A merchant processing between 1m and 6m VISA and MasterCard transactions p/a
Level 3: A merchant processing between 20k and 1m VISA and MasterCard transactions p/a
Level 4: A merchant processing less than 20k VISA and MasterCard transactions p/a
Any merchant that suffers a breach involving card payment data can be escalated to a higher compliance level.
How do I become PCI compliant?
To be PCI compliant, there are a set of 12 requirements set by the PCI Security Standards Council (PCI SSC) that are designed to ensure the highest level of protection for any data that is being used throughout the transaction process of a payment. This can be manually or electronically, but if organisations adhere to these requirements, they will dramatically improve their security against malicious attacks towards their organisation, including any internal risks.
There are specific reporting requirements based on your organisation’s merchant level, determined by the number of transactions made over a year.
Merchant Level 1: On-site assessment by a Qualified Security Assessor (QSA)
Merchant Levels 2 – 4: Self assessment via the Self-Assessment Questionnaires (SAQ)
You must also have a quarterly network scan by an Approved Scan Vendor and an attestation of Compliance Form.

